2013 Social Media Hacks Back to Bite Us: What to Know
Back in 2013, a series of cyber-attacks which plagued social media sites are now coming back to haunt us. Linked In, Tumblr and My Space were all hit in 2013 and millions of email addresses and passwords were stolen.
Until now, the extent of the breaches have not been confirmed and the stolen data had not been made public. But last month a hacker(s) which goes by the name of Peace has put the data up for sale on the dark web, the asking price ranges from just $150 (£103) for the Tumblr data to $2,000 (£1500) in bitcoin for the LinkedIn data. The differences in price likely has to do with level of encryption applied to the passwords.
Should I be bothered about three year old data?
If you have an account with any of these sites and you haven’t updated your password since 2013, then do so now. If you have used the same password elsewhere, change it on those sites as well. Be aware that even after changing your passwords you are still vulnerable to phishing schemes as the data obtained in the hacks contains un-encrypted email addresses.
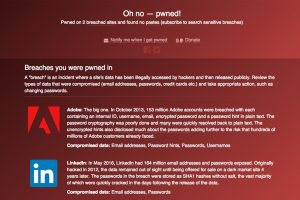
If you aren’t sure if your data has been compromised and you would like to know, Troy Hunt, an Australian security researcher has made it quick and easy to sift through the data dumps with his website ‘Have I been Pwned?’ You simply type in your e-mail address into the search box and it will sift through a data base of 617,828,599 compromised accounts from 109 attacked websites. If your email address was found then it will notify you as to which site it was obtained from.
If your email address is on the list, change the corresponding passwords and be extra vigilant with your email. Make sure your spam-filter settings are up to date and never click on any suspicious links within emails. Remember, the weakest link in our cyber-security is ourselves.
Further Reading:
What is Phishing and How Can It Be Avoided
What’s Your Weakest Link in Cyber Security?
Blast from the Past: the Malware Museum











Leave a Reply
Want to join the discussion?Feel free to contribute!